This post is a sidebar on an deep dive into domain redirects as it relates to Antifa.com redirecting to JoeBiden.com. If you haven’t already done so, please read the post titled Antifa Redirects to Joe Biden for context on why this part of the test was necessary and important.
There is a meme going around right now that says to type in antifa.com and see what happens. Spoiler: antifa redirects to Joe Biden. That is antifa.com redirects to joebiden.com.
The political right says this shows Biden’s support for antifa. The political left is claiming it’s just some prankster pointing a domain to a server to make a presidential candidate look bad.
Let’s avoid the politics and break it down technically and see what’s going on.
Associating a website with a domain
When a domain is registered, it has the option of having a website associated with it. To assign a website, the domain administrator must do three things:
- Establish a hosting platform somewhere
- Obtain an IP address for the server
- Associate the domain name with the IP address.
When a user requests a website, the domain name server (DNS) converts the website URL into a numerical address (the IP address) and then looks for the website at the server, retrieves the files, and displays the website.
When a web server responds to the request, it actually looks at the combination of host-header name (the URL) and the IP address to make sure that it’s serving the correct website. This allows multiple websites to be hosted on the same IP address. It is, however, possible to configure a server to respond to any domain requests with the files of the primary domain on that server. There are good reasons to do this and there are bad reasons to do this. And sometimes it misconfigured this way and nobody notices it until it’s too late.
Pointing a rogue domain to a server
Lets see what happens if we assign a domain name to the server that runs www.joebiden.com when that server is not accepting traffic for another domain. If the server accepts the domain request and redirects to joebiden.com, we’ll know that the redirection is open and it’s possible that any domain pointed to this server will redirect to www.joebiden.com. This would leave open the possibility that the antifa redirect is a prank or a malicious attempt to influence the election.
We’ll use our own domain name as test knowing for 100% sure that the domain and server are not affiliated in any way.
Pointing the unauthorized domain to the server
By quickly modifying the local hosts file, we can override the DNS cache and to set IP address for www.glimmernet.com to that of www.joebiden.com. This will point our local requests for www.glimmernet.com to the server running www.joebiden.com.
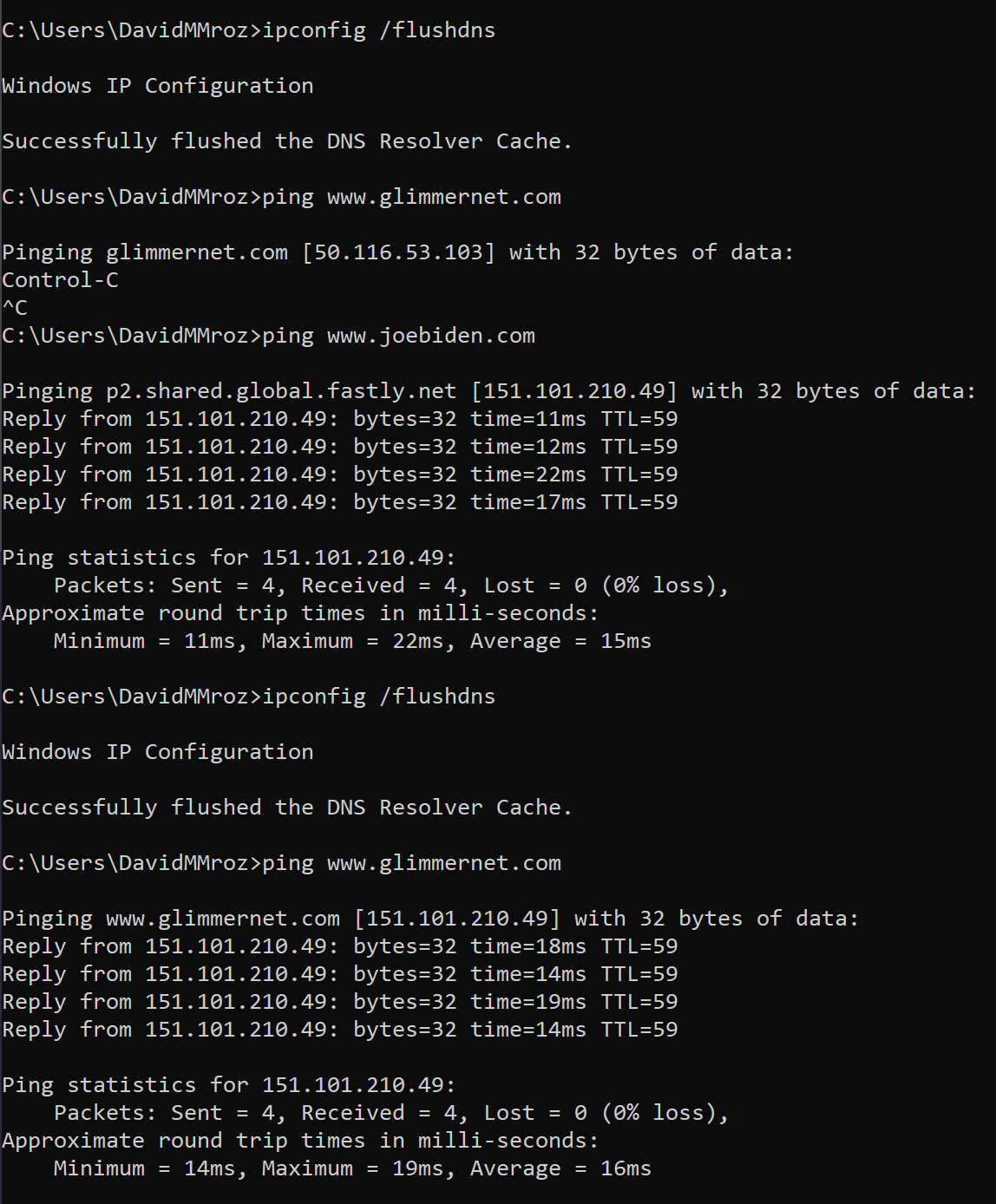
Now for the big test. If we try to load glimmernet.com, it’ll reference the server that hosts joebiden.com. We’ll either get a redirect to joebiden.com, we’ll get the address bar saying glimmernet.com but showing us joebiden.com, or we’ll get an error.
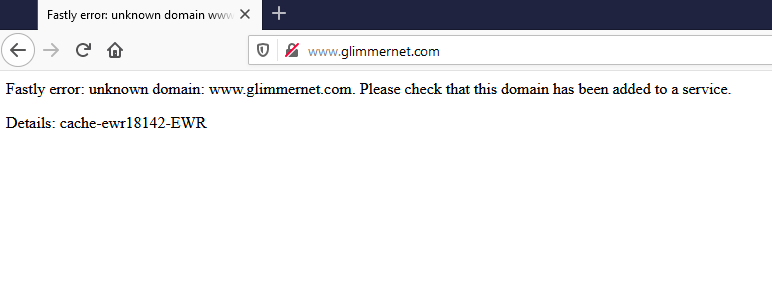
Fastly error: unknown domain: www.glimmernet.com. Please check that this domain has been added to a service.
Details: cache-ewr18154-EWR
Interesting
It didn’t accept the domain. In fact, it threw an explicit error that the domain has not been added to a service, meaning that this site will not serve up files for any domain that is not preconfigured on the site.
That confirms that the Fastly server will not respond to requests for glimmernet.com, but it doesn’t indicate one way the other what would happen if antifa.com is pointed to that server.
Let’s Try Antifa.com
Using the same local DNS trick, we can see if the server hosting joebiden.com will accept requests for antifa.com.
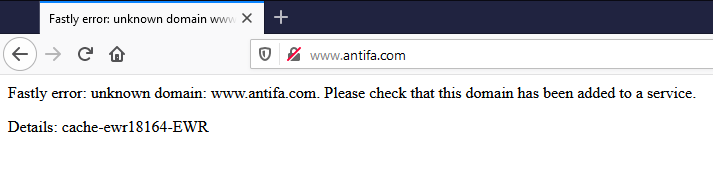
As we anticipated, it will not. The Fastly server hosting joebiden.com is not hosting antifa.com and will not respond to requests for antifa.com
But antifa.com is still redirecting to joebiden.com. Read the Antifa Redirects to Joe Biden post for more information on how this is happening and what it all means.






0 Comments